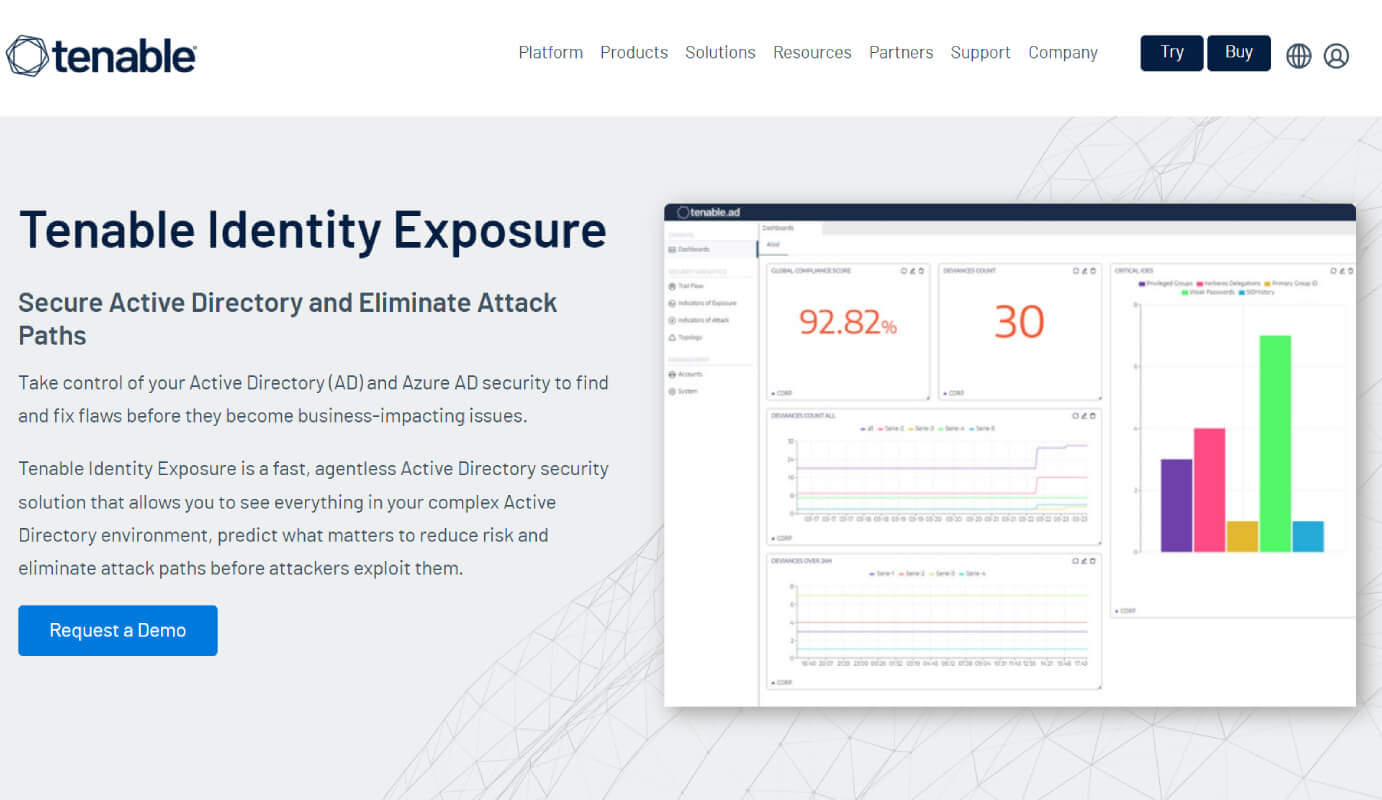
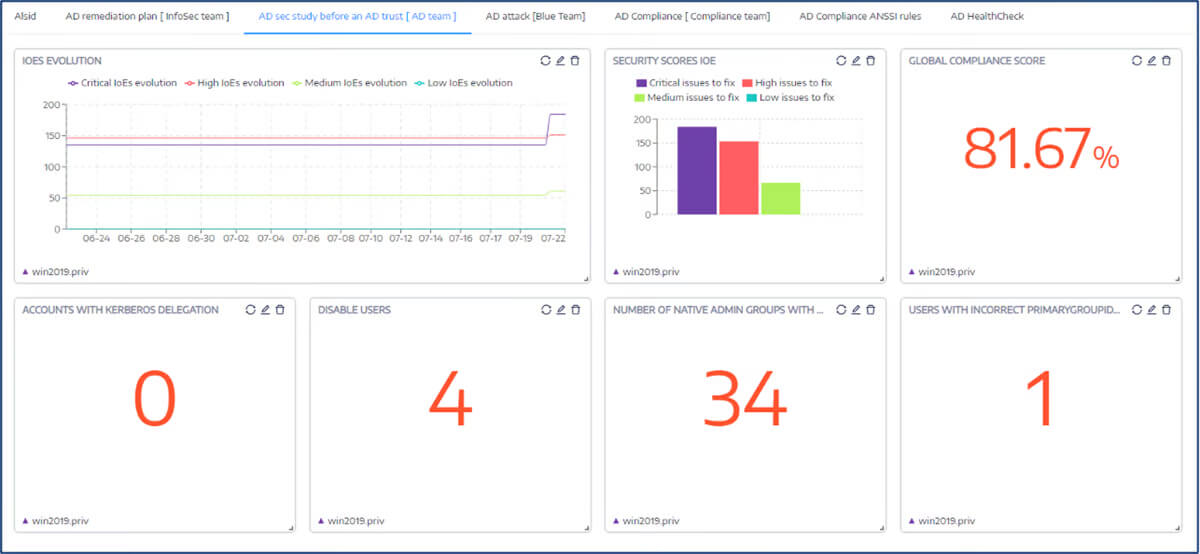
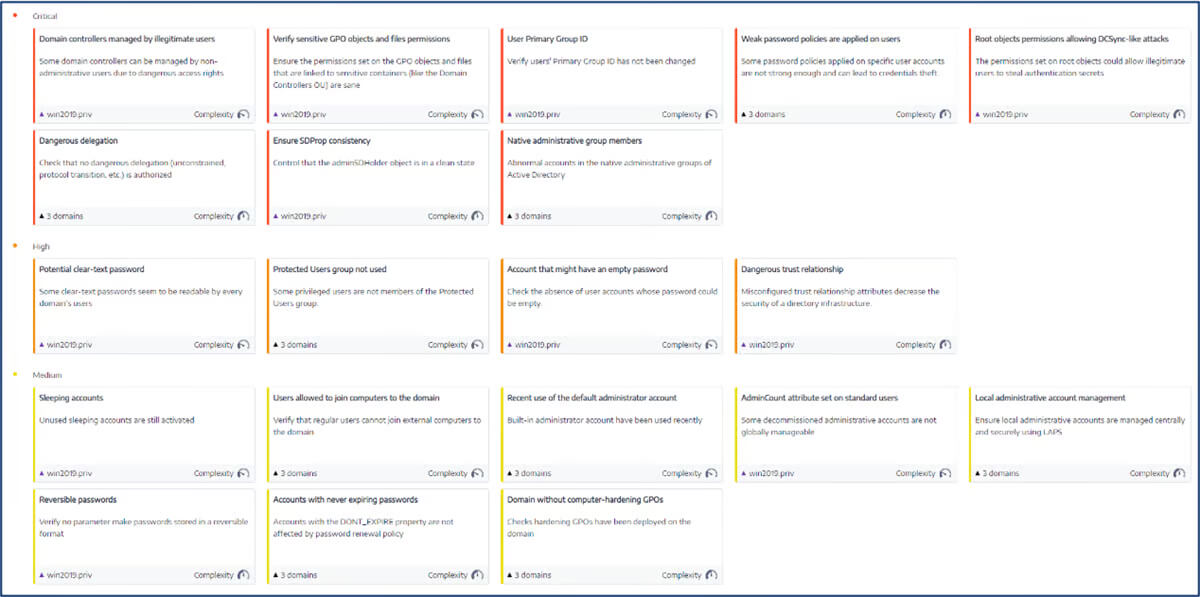
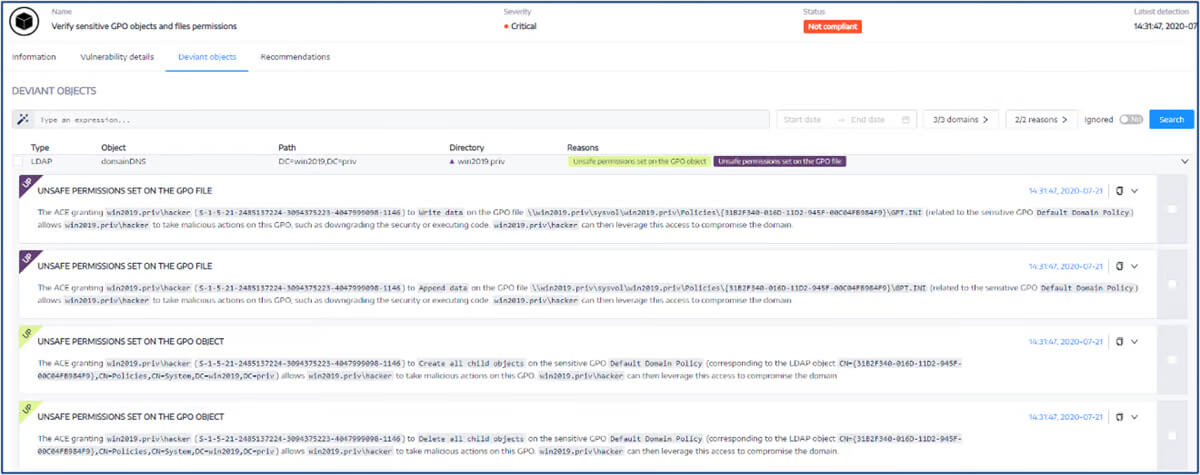
Tenable Identity Exposure Alternatives
26We've compiled a list of 26 free and paid alternatives to Tenable Identity Exposure. The primary competitors include Cloudflare, Datadog. In addition to these, users also draw comparisons between Tenable Identity Exposure and Tenable Cloud Security, Tenable Vulnerability Management, Tenable One. Also you can look at other similar options here: Cloud Security Software, Cloud Security Monitoring and Analytics Software.